IT User Access Control Database Log Template Word
The IT User Access Control Database Log Template Word is a comprehensive tool designed to help businesses keep track of user access to their databases. This template is perfect for businesses that want to ensure that their databases are secure and that only authorized personnel have access to sensitive information.
The template is easy to use and can be customized to meet the specific needs of your business. It includes fields for recording user information, such as name, job title, and department, as well as fields for recording the date and time of access, the type of access granted, and any notes or comments related to the access.
With this template, you can easily monitor user access to your databases and identify any unauthorized access attempts. This can help you prevent data breaches and ensure that your sensitive information remains secure.
The IT User Access Control Database Log Template Word is also a great tool for businesses that need to comply with regulatory requirements, such as HIPAA or PCI-DSS. By keeping detailed records of user access to your databases, you can demonstrate compliance with these regulations and avoid costly fines and penalties.
Overall, the IT User Access Control Database Log Template Word is an essential tool for any business that wants to ensure the security of their databases and protect their sensitive information. With its user-friendly design and customizable fields, this template is a must-have for businesses of all sizes.
IT User Access Control Database Log Template
The IT User Access Control Database Log Template keeps track of user ID, department, password, access privilege, and more. Users should have direct access only to services and information that they have been specifically authorized to use. Unless expressly authorized, access to all resources and services is denied. The Information Technology Security Manager should maintain ITSD106-2 IT USER ACCESS CONTROL DATABASE for that purpose.
Users must secure their equipment if it is to be unattended for any length of time. Screen locks should automatically activate after 15 minutes of inactivity (users may set screen locks to activate sooner and they should be allowed to activate screen locks immediately, if desired). All communications to external (i.e., Internet-based) resources by way of the company Information Technology network should be restricted to authorized users. Users should apply for permission to access external resources and access should be authorized on a case-by-case basis.
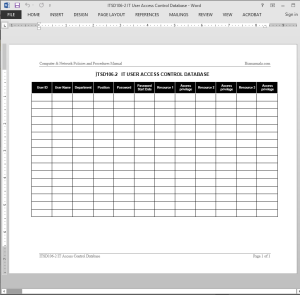 IT User Access Control Database Log Template Details
IT User Access Control Database Log Template Details
Pages: 01
Words: 28
Format: Microsoft Word 2013 (.docx)
Language: English
Manual: IT Policies and Procedures Templates
Category: IT Security & Disaster Recovery
Procedure: IT Access Control Procedure ITSD106
Type: Log




















Reviews
There are no reviews yet.