IT Access Control Log Template Word
The IT Access Control Log Template Word is a comprehensive tool designed to help organizations keep track of access control activities. This template is perfect for IT departments that need to monitor and manage access to sensitive information and systems.
The template is easy to use and customizable, allowing you to tailor it to your organization’s specific needs. It includes fields for recording user information, access requests, approvals, denials, and more. With this template, you can easily track who has access to what information and systems, and ensure that access is granted only to authorized personnel.
The IT Access Control Log Template Word is ideal for organizations that need to comply with regulatory requirements such as HIPAA, PCI-DSS, and SOX. It can also be used to support internal audits and security assessments, helping you identify potential vulnerabilities and areas for improvement.
By using this template, you can improve your organization’s security posture and reduce the risk of data breaches and other security incidents. It provides a centralized location for tracking access control activities, making it easier to identify and address potential issues before they become major problems.
Overall, the IT Access Control Log Template Word is an essential tool for any organization that takes security seriously. It is easy to use, customizable, and provides a comprehensive view of access control activities, helping you stay on top of your organization’s security posture and compliance requirements.
IT Access Control Log Template
Instances of access and use of any Information Technology resource should be automatically logged in the IT Access Control Log Template. ITSD106-3 ACCESS CONTROL LOG should be retained in accordance with legal and regulatory requirements. Access to applications should be limited to authorized users and to normal business hours, with reasonable exceptions.
Access control is defined as the enforcement of specified authorization rules based on positive identification of users and the systems or data they are permitted to access (or, providing access to authorized users while denying access to unauthorized users). The Information Technology Security Manager should periodically (once a week is recommended) review the Access Control Log and present a status report to Information Technology Managers.
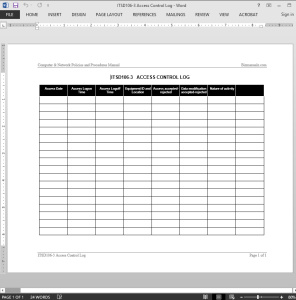 IT Access Control Log Template Details
IT Access Control Log Template Details
Pages: 01
Words: 24
Format: Microsoft Word 2013 (.docx)
Language: English
Manual: IT Policies and Procedures Templates
Category: IT Security & Disaster Recovery
Procedure: IT Access Control Procedure ITSD106
Type: Log




















Reviews
There are no reviews yet.