risk
Your customers want their products, and they want them now. In fact, 62% of consumers say delivery speeds influence their buying decisions, and 30% of consumers expect same-day shipping. To keep up with customer demand, you need efficient delivery routes to deliver more packages quickly. How can delivery routes be more efficient?
Read moreMany people struggle with just what a preventive action looks like and how it differs from a corrective action.
Read moreLeading indicators for safety performance are based on an examination of potential risks as well as past incidents that did not result in injury. This can include history such as observation, unsafe actions, and safety meeting attendance. In contrast, lagging safety indicators only look at past injuries. Leading indicators thus give you the ability to […]
Read morePutting an ISO 9001 Quality Management System in place is manageable when done is stages. Clause 7 record keeping is extensive, and it makes sense to save it for the last phase.
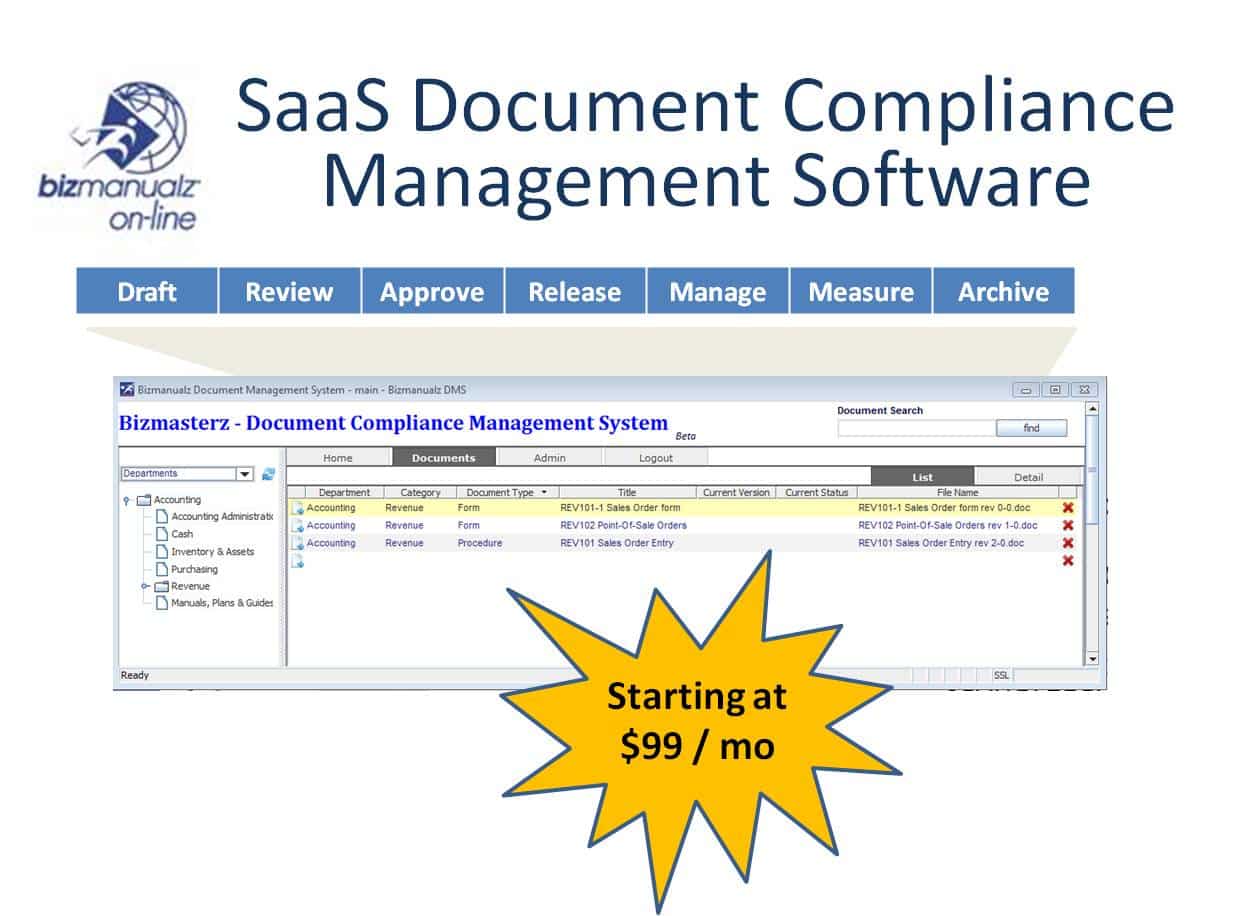
Read moreYour GRC program can be significantly enhanced with the addition of Policy and Procedure Management software.
Read moreFor a start-up company, financial strategies for business are important to cover a lot of expenses and to give you enough resources to keep on moving forward as you start generating profit–and here is where start-up business loans come in. From your working capital, inventory, to real estate and equipment, sometimes your funds on hand […]
Read moreTransferring cybersecurity monitoring functions to a third-party virtual contractor is not a new topic. Security Operations Center (SOC) functions outsourcing has become widespread practice not only for large companies but also for relatively small organizations. Key client questions have also changed. It is not about proving the need for outsourced SOCs per se. Customers are […]
Read moreWhat embezzlement techniques are considered the most common embezzlement schemes used by embezzlers?
Read moreControl over cash receipts and disbursement are a vital element of the company’s internal accounting controls. What Cash Cycle Procedures should you use?
Read more