IT Security Guide
The IT Security Guide comes with the IT Policies and Procedures Manual, it is vital for any organization today. IT security is all about securing and protecting your IT assets and information is likely your most prized asset. IT is pretty much a commodity these days, but your information is your business. Failure to secure information could have legal, economic or physical ramifications for your organization. It covers the following:
WHY INFORMATION SECURITY?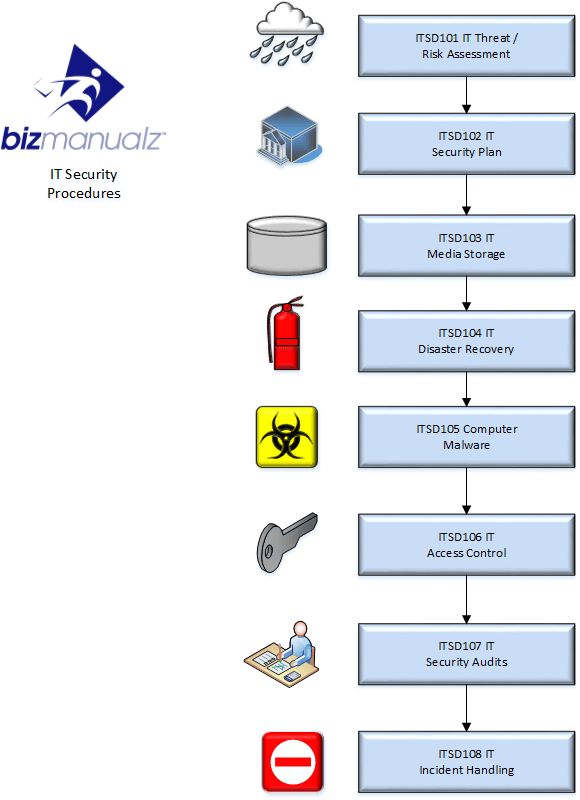
- A Brief History of Information Security
- What Information is At Risk?
- Why Company Executives Should Read These Guidelines
- A Final Word on Considering IT Security Issues
- Introductory Security Checklist
ASSESSING YOUR NEEDS
- Introduction to Risk Assessment
- Commonly Asked Questions
- Components of IT Risk
- Dealing with Computer Risk
- Guidelines for IT Risk Assessment
- Closing Thoughts on IT Risk Assessment
- IT Risk Assessment Checklist
INFORMATION SECURITY POLICY
- Why Do You Need IT Security Policies?
- Commonly Asked IT Security Questions
- How to Develop IT Security Policy
- From Board Room to Break Room: Implementing Security Policy
- Closing Thoughts on IT Security Policy
- IT Policy Development and Implementation Checklist
INFORMATION SECURITY MANAGEMENT
- Introduction to IT Security Management
- Commonly Asked Questions
- Nurturing Support within the Organization
- Planning for the Unexpected
- Testing and Review
- Implementation and Day-to-Day Maintenance
- IT Security Management Checklist
PROTECTING YOUR SYSTEM
- Introduction to Physical Security
- Commonly Asked Questions
- Physical Security Policy Issues
- Physical Security Checklist
INFORMATION SECURITY THREATS
- Introduction to Information Threats
- Commonly Asked Questions
- Information Threats Policy Issues
- Information Threats
- Information Security Countermeasures
- Information Security Checklist
SOFTWARE SECURITY
- Introduction to Software Security
- Commonly Asked Questions
- Software Security Policy Issues
- Software Threats (Examples)
- Software Security Countermeasures
- Software Security Checklist
USER ACCESS CONTROL
- Introduction to User Access Security
- Commonly Asked Questions
- User Access Policy Issues
- User Access Threats (Examples)
- User Access Security Countermeasures
- User Access Security Checklist
NETWORK (INTERNET) SECURITY
- Introduction to Network Security
- Commonly Asked Questions
- Network Security Policy Issues
- Network Threats (Examples)
- Network Security Countermeasures
- Closing Thoughts on Network Security
- Network Security Checklist
TRAINING: A NECESSARY INVESTMENT IN PEOPLE
- Introduction to IT Training
- Commonly Asked Questions
- Targeting IT Training Efforts
- How Does IT Security Affect the Workplace?
- IT Training Goals
- A Sample IT Training Outline
- IT Training Frequency
- Closing Thoughts on IT Security Training
- IT Security Training Checklist
- Computer Reference Materials







